QueryCon 2018
An osquery conference by Kolide
San Francisco | May 31 - Jun 1
QueryCon 2018 Videos
Nick Anderson (Facebook) - Evolving Our Open Source Community
An exploration of how the osquery community has grown, problems we faced/still face, and the directions we're hoping to push the community forward. Over the past two years the osquery community has increased dramatically. Not only have the number of contributions to the agent dramatically bumped, so has the number of platforms we support and richness of discussions in our community around best leveraging osquery. Nick takes us on a tour of where osquery has been and where it is headed.
Teddy Reed (Facebook)The Scary Parts of Osquery

Scott Lundgren (Carbon Black)An Outsider's Journey to Join the Osquery Community

Mitchell Grenier (Facebook)Catching Everything with Osquery Events
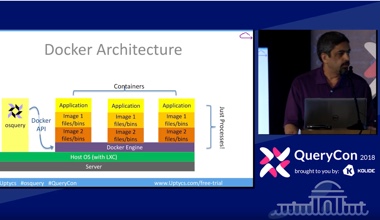
Milan Shah (UpTycs)Osquery and Docker Containers

Mike Myers (Trail of Bits)Extensions Skunkworks: Unconventional Uses for Osquery
Michael Lynn (Facebook)Fact Finding

Lauren Pearl (Trail of Bits)Three Super Features That Could Transform Osquery

Chris Long (Palantir)Practical System Auditing with Osquery

Ben Hughes (Stripe)Osquery, He Knows Me

Mike Arpaia (Kolide)fleetctl - Instrumenting Dynamic Environments

Rob Fry (JASK)SOC, aka Throw More People at the Problem

Henry Stamerjohann (Zentral)Osquery & Event Stream Processing Into ElasticStack

Samuel Keeley (Airbnb)The power of SQL: Complex queries at your fingertips
Join us for a 2-day Osquery conference at the Palace of Fine Arts Innovation Hangar focused on bringing security, devops, macadmins, and other experts in the Osquery community together. With talks from industry juggernauts and the creators of Osquery, discussion will focus on emergent topics that affect the landscape & development of Osquery.
Osquery Expertise for Big and Small
We've brought together the biggest names in the Osquery community to speak and discuss on a variety of use-cases and issues. No matter whether you are an Osquery expert or are installing it for the first time there is something for you:
Reserve your seat for QueryCon18 now!
Your pass gets you all of the following:
Full Conference Access
Registration grants you full access to our two-day single track conference, packed with Osquery experts ranging from the Osquery creators and leaders to major open-source contributors and community members.
Learn MoreAfter Hours Cocktail Party
After a long day of talks, spend time imbibing with Osquery leaders, contributors, speakers, and other conference goers at this attendee-only networking event. Drinks and delicious food are on us!
Learn MoreEntry to Osquery Workshop
Inspired by the talks? The community workshop lets you put your ideas into action in a communal setting where you can get hands-on experience guided by experts, collaborate on issues, and network with community members.
Learn MoreFeatured Speakers
Nick Anderson
Security Engineer








The Venue
QueryCon18 will be held at the Palace of the Fine Arts Innovation Hangar, minutes away from the Golden Gate Bridge. Parking will be validated for all conference goers.
Pre-Conference Learning
How Osquery is Built - Teddy Reed & Javier Marcos
Facebook's Osquery is a Linux and OS X intrusion detection and response tool. It supports 10 OS flavors and is continuously built for 8 of those. It is very important that the infrastructure used to test, build, and publish security software be secure itself. This discussion presents how our Security team has enabled any Github contributor to submit C/C++/bash code to our CI and build server, safely. We will guide the audience through our CI hardening process and the attack and vulnerability reports we have received through our bug bounty targeting CI. This includes isolating a Mac Mini fleet of build slaves, not trusting Jenkins as much as possible, automatically building, signing, and publishing packages to AWS S3, doing the same for OS X kernel extension code, adding 2-factor to everything.

Introduction to Osquery - Mike Arpaia

Monitoring macOS Hosts with Osquery - Zach Wasserman
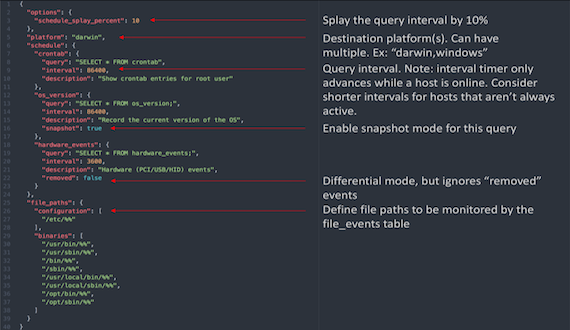
Osquery Across The Enterprise - Chris Long